smart card kerberos authentication Identity certificates used for Windows logon can generally be found: On the smart card itself. By requesting the certificates directly from the smart card issuer (either the CA or RA). By . NFL top-10 rankings: Chiefs top Lions; Steelers, Bills, Eagles climb; Falcons drop .
0 · Smart Cards and the Kerberos Protocol
1 · Smart Card and Remote Desktop Services
2 · Smart Card Technical Reference
3 · Smart Card Logon Integration with Kerb
4 · Smart Card Architecture
5 · Managing smart card authentication
6 · How Does Kerberos Work? The Authentication
7 · Configure Smart Card Logon on Windows Domains
8 · Chapter 11. Using Kerberos
9 · A primer on the Windows authentication process, Kerberos,
10 · 11.4. Setting up a Kerberos Client for Smart Cards
HID SEOS 8K MIFARE Classic MIFARE DESFire EV1 PROX: HID SEOS 8K .
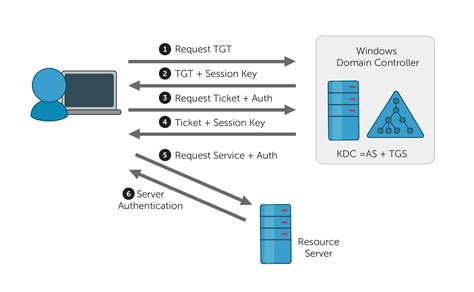
In a Remote Desktop scenario, a user is using a remote server for running services, and the smart card is local to the computer that the user is using. In a smart . See moreWhen the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a .
Identity certificates used for Windows logon can generally be found: On the smart card itself. By requesting the certificates directly from the smart card issuer (either the CA or RA). By . Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a . In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol. When a smart card is inserted, the smart card credential provider checks if it has a certificate, and for the certificate selected by the user, it offers to enter a PIN. The smart card .
Kerberos is an authentication protocol significantly safer than normal password-based authentication. With Kerberos, passwords are never sent over the network, even when .
Smart cards can be used with Kerberos, but it requires additional configuration to recognize the X.509 (SSL) user certificates on the smart cards: Install the required PKI/OpenSSL package, .You can use Ansible to enable smart card authentication for users whose certificates have been issued by the certificate authority (CA) of the domain that your Identity .
To sign in with a smart card from a computer that is not joined to a domain, the smart card must contain the root certification of the domain controller. A public key infrastructure (PKI) secure channel cannot be established without the root certification of the domain controller.
If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware.
Identity certificates used for Windows logon can generally be found: On the smart card itself. By requesting the certificates directly from the smart card issuer (either the CA or RA). By exporting the certificates from a third party application in which the certificates are already registered. Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol.When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a PIN, which is then sent to the smart card.
When a smart card is inserted, the smart card credential provider checks if it has a certificate, and for the certificate selected by the user, it offers to enter a PIN. The smart card replies whether the PIN matched or not.Kerberos is an authentication protocol significantly safer than normal password-based authentication. With Kerberos, passwords are never sent over the network, even when services are accessed on other machines.
Smart cards can be used with Kerberos, but it requires additional configuration to recognize the X.509 (SSL) user certificates on the smart cards: Install the required PKI/OpenSSL package, along with the other client packages: [root@server ~]# yum install krb5-pkinit.Active Directory (AD) users can authenticate with a smart card to a desktop client system joined to IdM and get a Kerberos ticket-granting ticket (TGT). These tickets can be used for single sign-on (SSO) authentication from the client. Prerequisites. The client is configured for smart card authentication. The krb5-pkinit package is installed. To sign in with a smart card from a computer that is not joined to a domain, the smart card must contain the root certification of the domain controller. A public key infrastructure (PKI) secure channel cannot be established without the root certification of the domain controller.
If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware.
Identity certificates used for Windows logon can generally be found: On the smart card itself. By requesting the certificates directly from the smart card issuer (either the CA or RA). By exporting the certificates from a third party application in which the certificates are already registered. Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers.
In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol.When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a PIN, which is then sent to the smart card.
When a smart card is inserted, the smart card credential provider checks if it has a certificate, and for the certificate selected by the user, it offers to enter a PIN. The smart card replies whether the PIN matched or not.Kerberos is an authentication protocol significantly safer than normal password-based authentication. With Kerberos, passwords are never sent over the network, even when services are accessed on other machines.Smart cards can be used with Kerberos, but it requires additional configuration to recognize the X.509 (SSL) user certificates on the smart cards: Install the required PKI/OpenSSL package, along with the other client packages: [root@server ~]# yum install krb5-pkinit.
Smart Cards and the Kerberos Protocol
Smart Card and Remote Desktop Services
Step 1 – Download the application NFC Tools by Wakedev on your iPhone or Android. Step 2 – .This item: 10PCS NTAG215 NFC Cards Blank NFC Tags RFID NFC Card NFC .
smart card kerberos authentication|Smart Card Technical Reference