smart card mitm Generative AI is making MITM attacks more prevalent because it’s now easier to trick unsuspecting users into a phishing dragnet. AFC/NFC wild card game: 8:15 p.m. . NFL conference championship round. Sunday, Jan. 26. NFC Championship Game: . The No. 3 seed hosts the No. 6 and the No. 4 .Stay up to date with your favorite team to see if they have a chance to make the 2024 playoffs. Seven teams from each conference will make it to the postseason. Check out which teams are .
0 · what is a mitm attack
1 · mitm encryption
$60.00
Generative AI is making MITM attacks more prevalent because it’s now easier to trick unsuspecting users into a phishing dragnet.
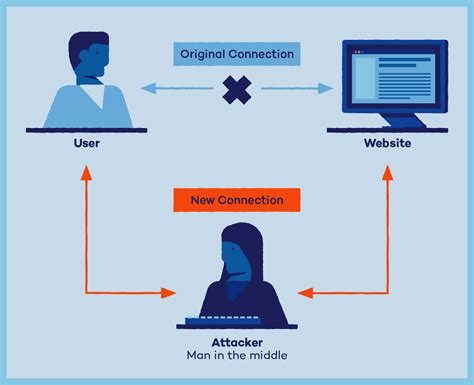
A man-in-the-middle (MitM) attack is a type of cyberattack in which communications between two parties is intercepted, often to steal login credentials or personal . The RDPDR channel is used for redirecting devices such as drives and smart cards from the client machine to the remote session. On the remote machine, the channel is handled by a filesystem driver that communicates with RDS over the TSVCPIPE pipe. Here’s a brief introduction to the protocol. Generative AI is making MITM attacks more prevalent because it’s now easier to trick unsuspecting users into a phishing dragnet. A man-in-the-middle (MitM) attack is a type of cyberattack in which communications between two parties is intercepted, often to steal login credentials or personal information, spy on.
MITM attacks often succeed by exploiting weak or misconfigured credential-based authentication methods like PEAP-MSCHAPv2. Using 802.1X with digital certificates eliminates credential-based vulnerabilities, providing strong encryption and authentication security.An overview of man-in-the-middle (MITM) attacks: what they are, how they work, the damage they can do, and why passwords won't stop them.
what is a mitm attack
A man-in-the-middle (MitM) attack is a form of cyberattack in which criminals exploiting weak web-based protocols insert themselves between entities in a communication channel to steal data. Here’s everything you need to know about MiTM schemes specifically, how to identify when your device is experiencing one, and how to protect your personally identifiable information (PII) and your device from cybercriminals.You can use several tools to test MITM attacks, such as a Wi-Fi pineapple, password-stealing tools, Kali Linux, MITMf, Wireshark, Cain &Abel, Ettercap, and additional tools like ARP spoofing, etc. Digital certificates help networks move away from credentials.
A man-in-the-middle (MitM) attack is a form of cyberattack where important data is intercepted by an attacker using a technique to interject themselves into the communication process. A man-in-the-middle attack (MITM attack) is a cyber attack where an attacker relays and possibly alters communication between two parties. The RDPDR channel is used for redirecting devices such as drives and smart cards from the client machine to the remote session. On the remote machine, the channel is handled by a filesystem driver that communicates with RDS over the TSVCPIPE pipe. Here’s a brief introduction to the protocol. Generative AI is making MITM attacks more prevalent because it’s now easier to trick unsuspecting users into a phishing dragnet.
A man-in-the-middle (MitM) attack is a type of cyberattack in which communications between two parties is intercepted, often to steal login credentials or personal information, spy on.
MITM attacks often succeed by exploiting weak or misconfigured credential-based authentication methods like PEAP-MSCHAPv2. Using 802.1X with digital certificates eliminates credential-based vulnerabilities, providing strong encryption and authentication security.An overview of man-in-the-middle (MITM) attacks: what they are, how they work, the damage they can do, and why passwords won't stop them.A man-in-the-middle (MitM) attack is a form of cyberattack in which criminals exploiting weak web-based protocols insert themselves between entities in a communication channel to steal data. Here’s everything you need to know about MiTM schemes specifically, how to identify when your device is experiencing one, and how to protect your personally identifiable information (PII) and your device from cybercriminals.
You can use several tools to test MITM attacks, such as a Wi-Fi pineapple, password-stealing tools, Kali Linux, MITMf, Wireshark, Cain &Abel, Ettercap, and additional tools like ARP spoofing, etc. Digital certificates help networks move away from credentials. A man-in-the-middle (MitM) attack is a form of cyberattack where important data is intercepted by an attacker using a technique to interject themselves into the communication process.

mitm encryption
Bring back the touch and feel of a record player with this modern take on it using a Raspberry Pi and an NFC reader. Installation runs three services: Read service (spawned by jukebox service) - This listens for NFC cards and plays spotify .SmartCard is the digital NFC business card of the future. Stay connected, share your passions, and drive more leads with just one tap. Make a lasting impression with SmartCard. . Sri Lanka’s first ever smart business card, trusted by top .
smart card mitm|mitm encryption