which of the following is a concern with rfid tagging An RFID tag can be affixed to an object and used to track tools, equipment, inventory, assets, people, or other objects. RFID offers advantages over manual systems or use of barcodes. The tag can be read if passed near a reader, even if it is covered by the object or not visible. The tag can be read inside a case, carton, box or other container, and unlike . Are you looking for wholesale outdoor use nfc reader? Our guard tour system list .
0 · what is rfid technology
1 · what is rfid tags
2 · rfid security threats
3 · rfid security problems
4 · rfid identification chart
5 · rfid badge identification
6 · retail rfid identification
7 · are rfid tags safe
2. The NFC tag must be NDEF formatted in order to work with the iPhone. Also make sure that you do not have a cover on the iPhone preventing the tag from working. I .Posted on Nov 1, 2021 12:10 PM. On your iPhone, open the Shortcuts app. Tap on the Automation tab at the bottom of your screen. Tap on Create Personal Automation. Scroll down and select NFC. Tap on Scan. Put .Posted on Nov 1, 2021 12:10 PM. On your iPhone, open the Shortcuts app. Tap on the Automation tab at the bottom of your screen. Tap on Create Personal Automation. Scroll down and select NFC. Tap on Scan. Put your iPhone near the NFC tag. Enter a name for your tag. .
what is rfid technology
An RFID tag can be affixed to an object and used to track tools, equipment, inventory, assets, people, or other objects. RFID offers advantages over manual systems or use of barcodes. The tag can be read if passed near a reader, even if it is covered by the object or not visible. The tag can be read inside a case, carton, box or other container, and unlike .
Some people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with .Tracking. By reading information received from RFID tag an attacker can track the location and movement of an object or a person. When a tag is attached to an object and the object enter the RFID reader’s field, the RFID read can identify . The use of RFID tags to track humans has been met with resistance due to privacy concerns. Poor physical security can result in tags being destroyed even if there is no specific gain for the attacker, leading to further risks associated with RFID technology.
is receiver another name for rfid reader
what is rfid tags
A primary RFID security concern is the illicit tracking of RFID tags. Tags, which are world-readable, pose a risk to both personal location privacy and corporate/military security. Such concerns have been raised with respect to the United States Department of Defense's recent [when?] adoption of RFID tags for supply chain management. [127]
Some people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID-enabled passport or a security access card with an RFID chip.Tracking. By reading information received from RFID tag an attacker can track the location and movement of an object or a person. When a tag is attached to an object and the object enter the RFID reader’s field, the RFID read can identify the object and locate its position. Another concern lies in that RFID tag data can be read by anyone with a compatible reader. Tags can often be read after an item leaves a store or supply chain. They can also be read without a user's knowledge via unauthorized readers. According to a recent RFID market report, the global market for RFID tags, readers and software is expected to reach .7 billion this year and expand to .4 billion by 2026. Here are some of the trends driving that growth.
For instance, Challenges of Low-Frequency RFID Tags. The size and cost of low-frequency RFID tags are elevated as they need a large dimension of antenna design. Moreover, these LF tags are resistive towards metal presence and non-ferrous metallic .
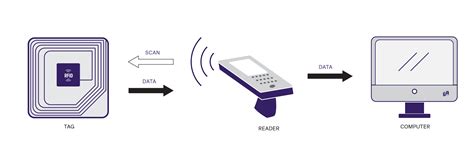
Description. Radio Frequency Identification (RFID) refers to a wireless system comprised of two components: tags and readers. The reader is a device that has one or more antennas that emit.There are two types of RFID tags as follows. 1. Passive tags (no internal power source, powered by the reader’s signal) 2. Active tags (powered by an internal battery and can transmit signals on their own). • RFID Reader: The reader emits radio waves through its antenna to power the passive RFID tag or to communicate with an active tag. Often the term "RFID" is loosely used to describe both, but there's a big difference between them: RF tags all send the same, simple signal and simply tell the receiver that something is present; RFID tags send more complex signals that uniquely identify whatever they're attached to.
The use of RFID tags to track humans has been met with resistance due to privacy concerns. Poor physical security can result in tags being destroyed even if there is no specific gain for the attacker, leading to further risks associated with RFID technology.A primary RFID security concern is the illicit tracking of RFID tags. Tags, which are world-readable, pose a risk to both personal location privacy and corporate/military security. Such concerns have been raised with respect to the United States Department of Defense's recent [when?] adoption of RFID tags for supply chain management. [127] Some people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID-enabled passport or a security access card with an RFID chip.
is the onn stick on wallet rfid blocking
Tracking. By reading information received from RFID tag an attacker can track the location and movement of an object or a person. When a tag is attached to an object and the object enter the RFID reader’s field, the RFID read can identify the object and locate its position.
Another concern lies in that RFID tag data can be read by anyone with a compatible reader. Tags can often be read after an item leaves a store or supply chain. They can also be read without a user's knowledge via unauthorized readers.
According to a recent RFID market report, the global market for RFID tags, readers and software is expected to reach .7 billion this year and expand to .4 billion by 2026. Here are some of the trends driving that growth.
For instance, Challenges of Low-Frequency RFID Tags. The size and cost of low-frequency RFID tags are elevated as they need a large dimension of antenna design. Moreover, these LF tags are resistive towards metal presence and non-ferrous metallic .Description. Radio Frequency Identification (RFID) refers to a wireless system comprised of two components: tags and readers. The reader is a device that has one or more antennas that emit.There are two types of RFID tags as follows. 1. Passive tags (no internal power source, powered by the reader’s signal) 2. Active tags (powered by an internal battery and can transmit signals on their own). • RFID Reader: The reader emits radio waves through its antenna to power the passive RFID tag or to communicate with an active tag.
rfid security threats

WayAround is now partnering with Accessible Pharmacy! Accessible Pharmacy is a comprehensive, home delivery pharmacy specializing in the blind, DeafBlind, and low vision community. Accessible Pharmacy provides accessible .For wine and spirits brands looking to experiment with NFC, reaching out to your label converter is a good place to start. Label converters will lead the charge for integrating NFC tags into product labels and other .
which of the following is a concern with rfid tagging|retail rfid identification