secure symmetric authentication for rfid tags report Starting with a short introduction into common RFD systems, we present a motivation why secure authentication with standardized symmetric crypto algorithms for RFID tags is necessary for . Smart Card Reader. Use your phone as contact-less smart card reader. Allow a host computer to use the smartphone's NFC hardware as contact-less. smartcard reader. On .I've tried an app called nfc relay, that was supposed to start a server and transmit data from my cellphone to my computer, but it also doesn't seems to work. Android phone, and Ubuntu 22.04 OS on my computer. 4. 3. Add a Comment.
0 · Strong Authentication for RFID Systems Using the AES
1 · Securing IoT
2 · Secure symmetric authentication for RFID tags
3 · Secure Symmetric Authentication for RFID Tags
4 · Secure Symmetric Authentication for RFID Tags
5 · ElProCus
6 · ESRAS: An efficient and secure ultra
7 · A Secure Authentication Scheme for RFID Systems☆
acr122u nfc reader writer. 13.56 Mhh support mifare 1k, ntag213, ultralight /ultralightc, Mifare plus, Mifare desfire. provide SDK and free nfc tool software. 5 pcs ntag213 nfc tag samples and 2 pcs UID MF1 card. IEC14443A and ISO18092 protocol compliance.
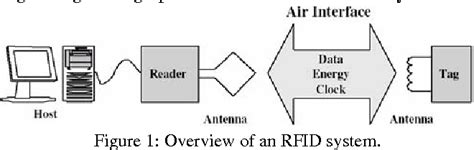
The project ART proposes to enhance passive RFID (Radio Frequency Identification) tags with cryptographically secure authentication. Targeting RFID tag with short tag ID, we employ a resource friendly symmetric encryption scheme, which is a stream cipher building block to enhance the security features in .
Starting with a short introduction into common RFD systems, we present a motivation why secure authentication with standardized symmetric crypto algorithms for RFID tags is necessary for .
in season standings
However, the RFID techniques are plagued to security and privacy issues due to underlying wireless communication channel. In order to come up with a solution, we propose . Recently, many solutions were proposed to secure RFID systems and many such systems are based on only lightweight primitives, including symmetric encryption, hash . In an RFID system, mutual authentication is considered one of the primary security requirements that should be accomplished between tag and server over a secure .Authentication for Long-range RFID Technology. Feldhofer, M., Dominikus, S. & Aigner, M. J. 1/09/03 → 31/08/05. Project: Research project
Semantic Scholar extracted view of "Secure Symmetric Authentication for RFID Tags" by Anuj Kumar et al.
Strong Authentication for RFID Systems Using the AES
In this paper, we demonstrate how the project ART (Authentication for long-range RFID systems) proposes to improve current RFID systems by providing secure authentication. The project is performed by four independent partners, two from industry and two academic partners.The project ART proposes to enhance passive RFID (Radio Frequency Identification) tags with cryptographically secure authentication.

Targeting RFID tag with short tag ID, we employ a resource friendly symmetric encryption scheme, which is a stream cipher building block to enhance the security features in active type RFID.Starting with a short introduction into common RFD systems, we present a motivation why secure authentication with standardized symmetric crypto algorithms for RFID tags is necessary for many applications. We demonstrate vulnerabilities of current RFID systems and explain how application of an authentication mechanism can solve them.
In contrast to the RFID community, which claims that cryptographic components are too costly for RFID tags, we describe a so-lution using strong symmetric authentication which is suitable for today’s requirements regarding low power consumption and low die-size.
However, the RFID techniques are plagued to security and privacy issues due to underlying wireless communication channel. In order to come up with a solution, we propose an efficient authentication scheme which uses pseudorandom number generators (PRNG) and some simple cryptographic operations. Recently, many solutions were proposed to secure RFID systems and many such systems are based on only lightweight primitives, including symmetric encryption, hash functions, and exclusive OR operation.
In an RFID system, mutual authentication is considered one of the primary security requirements that should be accomplished between tag and server over a secure communication channel. RFID authentication schemes must always be secure, efficient, and robust against well-known malicious security attacks [26] .
Authentication for Long-range RFID Technology. Feldhofer, M., Dominikus, S. & Aigner, M. J. 1/09/03 → 31/08/05. Project: Research project Semantic Scholar extracted view of "Secure Symmetric Authentication for RFID Tags" by Anuj Kumar et al.In this paper, we demonstrate how the project ART (Authentication for long-range RFID systems) proposes to improve current RFID systems by providing secure authentication. The project is performed by four independent partners, two from industry and two academic partners.
The project ART proposes to enhance passive RFID (Radio Frequency Identification) tags with cryptographically secure authentication. Targeting RFID tag with short tag ID, we employ a resource friendly symmetric encryption scheme, which is a stream cipher building block to enhance the security features in active type RFID.
nflk standings
Starting with a short introduction into common RFD systems, we present a motivation why secure authentication with standardized symmetric crypto algorithms for RFID tags is necessary for many applications. We demonstrate vulnerabilities of current RFID systems and explain how application of an authentication mechanism can solve them.In contrast to the RFID community, which claims that cryptographic components are too costly for RFID tags, we describe a so-lution using strong symmetric authentication which is suitable for today’s requirements regarding low power consumption and low die-size. However, the RFID techniques are plagued to security and privacy issues due to underlying wireless communication channel. In order to come up with a solution, we propose an efficient authentication scheme which uses pseudorandom number generators (PRNG) and some simple cryptographic operations. Recently, many solutions were proposed to secure RFID systems and many such systems are based on only lightweight primitives, including symmetric encryption, hash functions, and exclusive OR operation.

In an RFID system, mutual authentication is considered one of the primary security requirements that should be accomplished between tag and server over a secure communication channel. RFID authentication schemes must always be secure, efficient, and robust against well-known malicious security attacks [26] .Authentication for Long-range RFID Technology. Feldhofer, M., Dominikus, S. & Aigner, M. J. 1/09/03 → 31/08/05. Project: Research project
Securing IoT
Secure symmetric authentication for RFID tags
nfl scores today standings
Secure Symmetric Authentication for RFID Tags
The Dana Show. Dana Loesch is the number one nationally-syndicated female talk radio host in the country and hosts her award-winning show, The Dana Show, from Dallas, Texas. Read More ». January 14, 2021 No Comments.
secure symmetric authentication for rfid tags report|Secure Symmetric Authentication for RFID Tags