privacy challenges of rfid tags A generic challenge-response RFID protocol can be defined as in Fig. 1 where k is private information such as a tag’s secret key and ID. In order to facilitate the privacy . ACS ACR1552U USB NFC Reader IV (USB Type-A), W128445488 ((USB Type-A)) .
0 · what is rfid technology
1 · what is rfid tags
2 · rfid tags and privacy
3 · rfid tags and data protection
4 · rfid privacy and security
5 · rfid data protection
6 · rfid and privacy issues
7 · gdpr rfid tags
An Android NFC app for reading, writing, analyzing, etc. MIFARE Classic RFID tags. . Android examples of sensors and input. . Code Issues Pull requests android nfc-card .One Device pretends to be a NFC Card with Host Card Emulation (HCE) and the other device reads/writes to it as if it was a normal Type 4 NFC card. There are some complications if one device still has Android Beam but using the enableReaderMode NFC API .
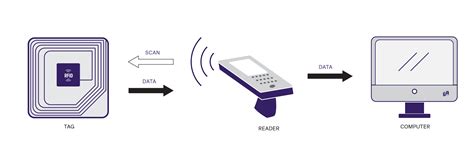
RFID Privacy Issues and Technical Challenges. Cheap tags and technology simple and secure enough to ensure personal data privacy are required before retailers implement .
Privacy of RFID systems is receiving increasing attention in the RFID community. Basically, t. RFID tags and the General Data Protection Regulation - personal data or not? RFID tags can be considered, under the General Data Protection Regulation 2018 (GDPR), an .
A generic challenge-response RFID protocol can be defined as in Fig. 1 where k is private information such as a tag’s secret key and ID. In order to facilitate the privacy .
The privacy issues and the technical challenges faced by the RFID tags in becoming a fundamental technology are discussed. Two notable privacy issues include . Privacy of RFID systems is receiving increasing attention in the RFID community. Basically, there are two kinds of RFID privacy notions in the literature: one based on the .The use of RFID in consumer and commercial environments raises significant data privacy challenges. One key concern is the unauthorized tracking of individuals. This paper surveys recent technical research on the problems of privacy and security for radio frequency identification (RFID). RFID tags are small, wireless devices that .
Use of RFID technology should be as transparent as possible, and consumers should know about the implementation and use of any RFID technology (including tags, readers and storage of . RFID Privacy Issues and Technical Challenges. Cheap tags and technology simple and secure enough to ensure personal data privacy are required before retailers implement .
RFID tags and the General Data Protection Regulation - personal data or not? RFID tags can be considered, under the General Data Protection Regulation 2018 (GDPR), an .
what is rfid technology
what is rfid tags
where is the rfid chip implanted
Security issues in RFID system. The RFID scheme consists of several classes of tags and reader. These tags include an inadequate amount of memory and low-power . A generic challenge-response RFID protocol can be defined as in Fig. 1 where k is private information such as a tag’s secret key and ID. In order to facilitate the privacy . The privacy issues and the technical challenges faced by the RFID tags in becoming a fundamental technology are discussed. Two notable privacy issues include .
Privacy of RFID systems is receiving increasing attention in the RFID community. Basically, there are two kinds of RFID privacy notions in the literature: one based on the .The use of RFID in consumer and commercial environments raises significant data privacy challenges. One key concern is the unauthorized tracking of individuals. This paper surveys recent technical research on the problems of privacy and security for radio frequency identification (RFID). RFID tags are small, wireless devices that .
Use of RFID technology should be as transparent as possible, and consumers should know about the implementation and use of any RFID technology (including tags, readers and storage of . This paper surveys recent technical research on the problems of privacy and security for radio frequency identification (RFID). RFID tags are small, wireless devices that .
RFID Privacy Issues and Technical Challenges. Cheap tags and technology simple and secure enough to ensure personal data privacy are required before retailers implement .
RFID tags and the General Data Protection Regulation - personal data or not? RFID tags can be considered, under the General Data Protection Regulation 2018 (GDPR), an . Security issues in RFID system. The RFID scheme consists of several classes of tags and reader. These tags include an inadequate amount of memory and low-power . A generic challenge-response RFID protocol can be defined as in Fig. 1 where k is private information such as a tag’s secret key and ID. In order to facilitate the privacy .
The privacy issues and the technical challenges faced by the RFID tags in becoming a fundamental technology are discussed. Two notable privacy issues include . Privacy of RFID systems is receiving increasing attention in the RFID community. Basically, there are two kinds of RFID privacy notions in the literature: one based on the .The use of RFID in consumer and commercial environments raises significant data privacy challenges. One key concern is the unauthorized tracking of individuals. This paper surveys recent technical research on the problems of privacy and security for radio frequency identification (RFID). RFID tags are small, wireless devices that .
Use of RFID technology should be as transparent as possible, and consumers should know about the implementation and use of any RFID technology (including tags, readers and storage of .
rfid chips sweden
rfid tags and privacy
Your entitlements should be located in a file named NFCTagReaders.entitlements and it should contains the following : .
privacy challenges of rfid tags|rfid tags and data protection