match each smart card attack on the left Match each smart card attack on the left with the appropriate description on the . Cloning isn't necessary as the algorithm used for nfc with the emv cards is .
0 · Test Out 2
1 · Security Pro 6.6.13 Section Quiz Flashcards
2 · Section 6 & 7 Quiz (docx)
3 · Logical Attacks
4 · Attacks against Smart Cards: Hands On Session
5 · Attacking smart cards in active directory
6 · 8.14.7 Flashcards
7 · 6.6.13 Practice Questions Flashcards
8 · 5.pdf
9 · 2.12 Flashcards
If you manage to crack all the keys you can see the HEX encoded contents of the key on your terminal and also in the output file output.mfd. # mfoc -O output.mfd. Found Mifare Classic 1k tag. ISO/IEC 14443A (106 kbps) target: ATQA .
Match each smart card attack on the left with the appropriate description on the .
Match each smart card attack on the left with the appropriate description on the right.Match each smart card attack on the left with the appropriate description on the right. Match each smart card attack on the left with the appropriate description on the . Match each smart card attack on the left with the appropriate description on the .
Match the general attack strategy on the left with the appropriate description on the right. (Each .
Test Out 2
Security Pro 6.6.13 Section Quiz Flashcards
Logical attacks against smart card can be classified in two categories: ill-typed applications or . First one, try to attack the smart card directly by forging a certificate with an .Match each smart card attack on the left with the appropriate description on the right.Match each smart card attack on the left with the appropriate description on the right. Software .
Smart card operating systems and software applications are vulnerable to classical attacks . Match each smart card attack on the left with the appropriate description on the right.Match each smart card attack on the left with the appropriate description on the right.
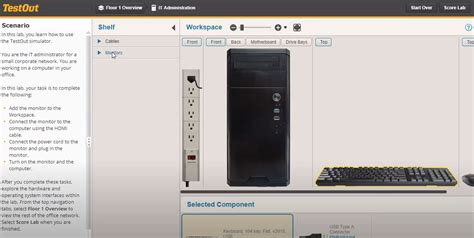
Match each smart card attack on the left with the appropriate description on the right. Match each smart card attack on the left with the appropriate description on the right.
Section 6 & 7 Quiz (docx)
Match the general attack strategy on the left with the appropriate description on the right. (Each attack strategy may be used once, more than once, or not all.) Stealing information.Logical attacks against smart card can be classified in two categories: ill-typed applications or well-typed applications. But the second category can also be split into permanent well-
First one, try to attack the smart card directly by forging a certificate with an arbitrary SAN. Unless you have a way to break RSA you should not be able to do this. Second; attack the Active Directory environment by modifying the UPN of a victim user to the value of the SAN in your legitimate smart card (i.e. switch the UPN for the victim for .Match each smart card attack on the left with the appropriate description on the right.Match each smart card attack on the left with the appropriate description on the right. Software Attacks Fault Generation Eavesdropping MicroprobingSmart card operating systems and software applications are vulnerable to classical attacks directed at software residing on a personal computer or server. Modern smart card operating systems allow applications to be uploaded onto a smart card after the card issuance.
my card nfc aptoide
Match each smart card attack on the left with the appropriate description on the right.Match each smart card attack on the left with the appropriate description on the right. Match each smart card attack on the left with the appropriate description on the right. Match each smart card attack on the left with the appropriate description on the right.
Match the general attack strategy on the left with the appropriate description on the right. (Each attack strategy may be used once, more than once, or not all.) Stealing information.Logical attacks against smart card can be classified in two categories: ill-typed applications or well-typed applications. But the second category can also be split into permanent well- First one, try to attack the smart card directly by forging a certificate with an arbitrary SAN. Unless you have a way to break RSA you should not be able to do this. Second; attack the Active Directory environment by modifying the UPN of a victim user to the value of the SAN in your legitimate smart card (i.e. switch the UPN for the victim for .
Match each smart card attack on the left with the appropriate description on the right.Match each smart card attack on the left with the appropriate description on the right. Software Attacks Fault Generation Eavesdropping Microprobing

Logical Attacks
2.3.1. Writing with NFC21 tools and NFC Reader / Writer. Using a connected NFC Writer and the Software NFC21 Writer, you can write URLs, text or business cards to NFC tags. Write protection can also be set up. With the .
match each smart card attack on the left|Attacks against Smart Cards: Hands On Session